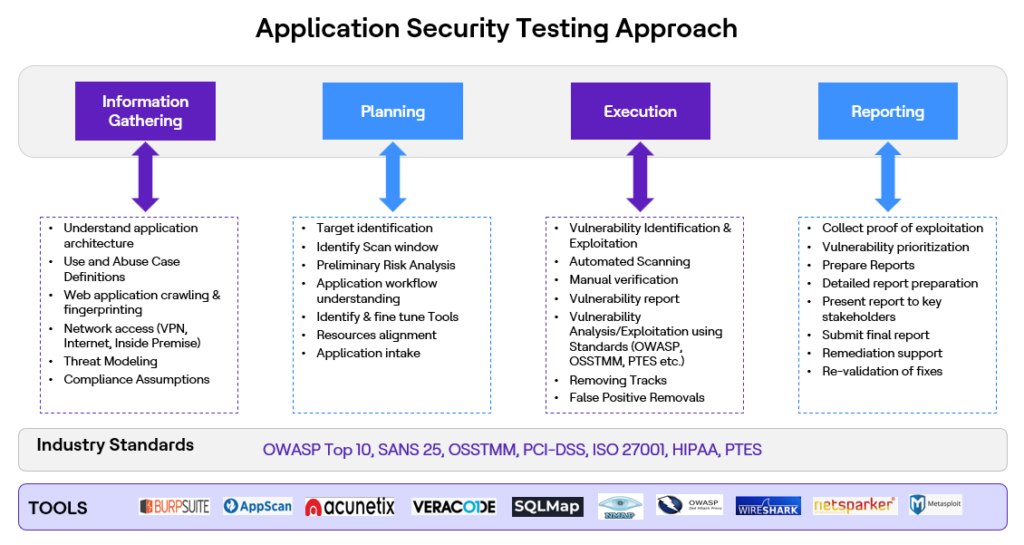
Web Application Vulnerability Assessment involves a Hybrid testing approach, meaning both Automated/tool based and Manual security tests are conducted concurrently based on the Industry Standards requested by the Application SMEs. After the completion of Hybrid test, Security Analyst filters false positives from the tool generated report, conducts manual analysis and prepares the final deliverables which will be shared to the relevant stakeholders and Application SMEs. The strategy of security testing is built-in in the software development lifecycle (SDLC) of the application and consists of the following phases:
REQUIREMENTS and USE CASE PHASE
Review policies and standards
On this stage a test engineer makes sure that there are appropriate policies, standards, and documentation in place. The entry point of this process is a list of all needed documents that describe general requirements to the security in the given business area as well as on the project level (process, technical, environment security requirements).
Develop measurement and metrics criteria
On this stage types of measurements are planned and the metrics to be collected are defined. The goal of this process is to focus on the most important aspects of the application security.
Security requirements analysis
Security requirements analysis is a very critical part of the testing process. On this stage a test engineer should understand what exactly security requirements are on the project. Also gaps that exist in the requirements are revealed during the process of analysis. The security properties which are investigated during this process are the following:
- User management
- Authentication
- Authorization
- Data confidentiality
- Integrity
- Accountability
- Session management
- Transport security
- Tiered System Segregation
- Privacy
PLANNING PHASE
Review design and architecture
This type of testing relates to static manual testing and implies that a test engineer reviews the design and architecture to find flaws that can result in insecure behavior of the application. During the review, a test engineer employs the following methodologies:
- The Comprehensive Method for Architecture Evaluation or
- Independent Software Architecture Review methodology.
List of metrics: Number of flaws found
Create and review threat tree
A threat tree is created to break down threats into testable tasks that can be processed easily. The tree depicts the way what basic threats the application may face. It can be transformed into atomic test tasks and integrated in the project plan.
List of metrics: Number of threats
DEVELOPMENT & EXECUTION PHASE
Static Analysis
Static analysis is so a called white-box method of testing that allows finding all inconsistencies and errors that cannot be found using black-box methods and often leads to revealing critical vulnerabilities. It includes:
- Source code analysis. This type of testing is going to be done automatically with help of source code analyzer.
- Code review. The code review is done by the testing team to identify all the flaws that were left after automatic analysis. It also allows to investigate risky code deeper.
List of metrics collected on this stage:
- % of code inherited from other projects
- % of code used from 3-rd party suppliers
- Number of vulnerabilities found
Dynamic Analysis
Dynamic type of testing supposes that the application has been run on the definite environment, in contrast with static types of testing.
Penetration Testing – Penetration testing is going to be done in two ways: automatically and manually.
- Manually using the procedures developed for a particular application and type of threat. or
- Automatically using
- web application vulnerability scanners,
- binary analysis tools,
- proxy tools.
Test Cases will be written to identify potential vulnerabilities and the main attacks to be performed during penetration testing are listed below:
- Injections
- Broken authentication and session management
- XSS (Cross site scripting)
- Insecure direct object reference
- Security misconfiguration
- Sensitive data exposure
- Missing function level access control
- Cross site request forgery (CSRF)
- Using Components with known vulnerabilities
- Unvalidated redirects and forwards
Metrics that are collected on the dynamic testing stage:
- Number of vulnerabilities found (by features, lines of code, etc.)
TEST REPORTS
Test results are sent to all interested parties and can contain:
- List of features which were tested
- List of vulnerabilities found during testing
- List of executed test cases with their statuses
- List of risks which were defined during testing
- Conclusion about the quality of the product

