Security Testing is a type of Software Testing and comes under Non-functional Testing. It detects vulnerabilities, threats, risks in a software application and prevents malicious attacks from intruders or hackers. The purpose of Security Tests is to identify all possible loopholes and weaknesses of the software system which might result in a loss of information, revenue, repute at the hands of the employees or outsiders of the Organization.
The goal of security testing is to identify the threats in the system and measure its potential vulnerabilities, so the system does not stop functioning or is exploited. It also helps in uncovering all possible security risks in the system and help developers in fixing these problems through coding.
Security testing takes the following six measures to provide a secured environment −
- Confidentiality − It protects against disclosure of information to unintended recipients.
- Integrity − It allows transferring accurate and correct desired information from senders to intended receivers.
- Authentication − It verifies and confirms the identity of the user.
- Authorization − It specifies access rights to the users and resources.
- Availability − It ensures readiness of the information on requirement.
- Non-repudiation − It ensures there is no denial from the sender or the receiver for having sent or received the message.
Most of the companies perform security testing on newly deployed or developed software, and network or information system environment.
Examples: Spotting a security flaw in a web-based application involves complex steps and creative thinking. At times, a simple test can expose the most severe security risk. You can try this very basic test on any web application −
- Log into the web application using valid credentials.
- Log out of the web application.
- Click the BACK button of the browser.
- Verify if you are asked to log in again or if you are able go back to the logged in page again.
“Security means that authorized access is granted to protected data and unauthorized access is restricted”. So, it has two major aspects; first is the protection of data and the second one is access to that data.
- A password should be in encrypted format
- Application or System should not allow invalid users
- Check cookies and session time for application
- For financial sites, the Browser back button should not work.
Focus Areas for Security Testing
There are four main focus areas to be considered in security testing (Especially for web sites/applications):
- Network security: It involves looking for vulnerabilities in the network infrastructure (resources and policies).
- System software security: It involves assessing weaknesses in the various software (operating system, database system, and other software) the application depends on.
- Client-side application security: It deals with ensuring that the client (browser or any such tool) cannot be manipulated.
- Server-side application security: It involves making sure that the server code and its technologies are robust enough to fend off any intrusion.
Application Security Testing
Application security (AppSec) testing is the process of making applications more resistant to security threats, by identifying security flaws/weaknesses and vulnerabilities in source code. it also help to detects security risks in a software application and prevents malicious attacks from intruders.
Application security (AppSec) is the processes, practices, and tools used to identify, repair, and protect the application against vulnerabilities in throughout the SDLC. Application security involves various tools (open-source & commercial) and methodologies to identify weaknesses and vulnerabilities and fix them before they can be exploited.
Application Security testing (AST) can be performed using both manual and automated using security testing tools and techniques. Security testing reviews the existing system to find unknown vulnerabilities. Most of organizations use a combination of several application security tools by leveraging Manual and Automation techniques.
Types of Application Security Testing (AST)
There are various types of application security testing to be performed as per industry standards and guidelines are explained as below:
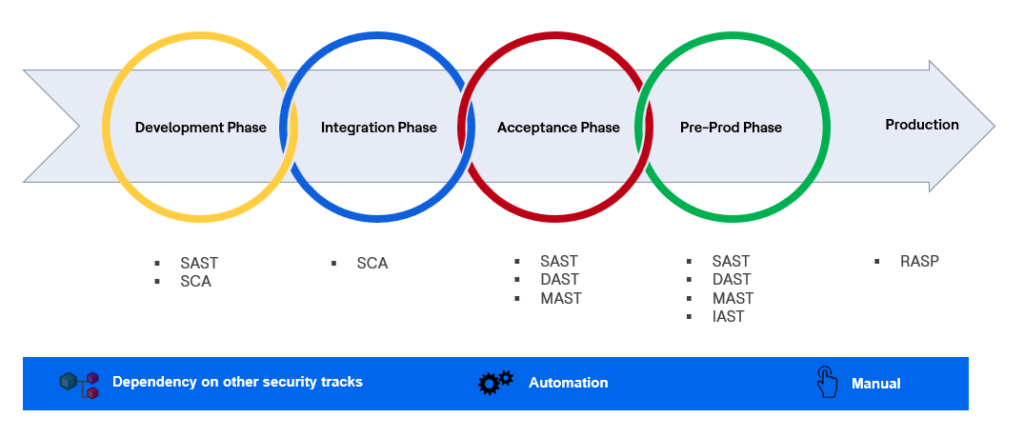
Static Application Security Testing (SAST)
SAST is performed to analyze application source code, byte code and binaries for coding and design conditions that are indicative of security vulnerabilities. SAST is a white box method of testing, it examines the code to find software flaws and weaknesses such as syntax errors, math errors, input validation issues, invalid or insecure references, SQL injection and others listed in the OWASP Top 10.
Tools: SonarQube, Checkmarx and other similar tools
Dynamic Application Security Testing (DAST)
DAST is performed to analyze E2E application security on a running application when all modules are integrated. DAST is a black box testing method that examines an application as it’s running to find vulnerabilities that an attacker could exploit. DAST include issues with query strings, requests and responses, the use of scripts, cookie and session handling, authentication, execution of third-party components, data injection, and DOM injection.
DAST tools (Burp Suite, AppScan, Veracode, Qualys etc.) can be used to conduct application scans simulating a large number of false positive or malicious use cases and reporting on the application’s response.
Interactive Application Security Testing (IAST)
IAST helps to perform automate web security testing in DevOps pipelines. IAST automatically retests identified vulnerabilities and validates whether they are real and can be exploited. It provides more accuracy than traditional dynamic testing and provides a real-time view of the top security vulnerabilities.
IAST tools (AppScan, Veracode etc. ) run dynamically and analyze software application during runtime. IAST tools can provide valuable information about the root cause of vulnerabilities and the specific lines of code that are affected, making remediation much easier. They can analyze source code, data flow, configuration and third-party libraries, and are suitable for API testing.
Software Composition Analysis (SCA)
SCA is done to identify Security Risks in Open Source Packages. SCA tools (Veracode, AppScan, Qualys etc.) help organizations to identify all open source packages in an application and all the known vulnerabilities of those packages.
Enterprise level applications can use thousands of third-party components, which may contain security vulnerabilities. SCA helps developers to understand which components and versions are actually being used, identify the vulnerabilities in their code to fix them before they are exploited.
Mobile Application Security Testing (MAST)
MAST is conducted to validate a mobile app in ways that a malicious user would try to attack it. Effective mobile security testing begins with an understanding of the application’s business purpose and the types of data it handles. They can test for security vulnerabilities like SAST, DAST and IAST, and in addition address mobile-specific issues like jailbreaking, malicious WiFi networks, and data leakage from mobile devices.
Mobile app security testing is performed to secure applications from external threats like malware and other digital frauds that risk critical personal and financial information from hackers. Any breach in mobile app security can not only give the access to hackers on user’s personal life in real-time but also disclose data like their current location, banking information, personal information, and much more. Key tools (ZAP, QARK, Drozer, MobSF, Veracode etc.) support MAST.
Runtime Application Self-Protection (RASP)
RASP is a security solution designed to provide personalized protection to applications in real-time. RASP tools (Fortify, OpenRASP, Signal Sciences etc.) evolved from SAST/ DAST/ IAST, and integrate with applications to analyze traffic and user behavior at runtime, to detect and prevent cyber threats.
RASP has visibility into application source code and can analyze weaknesses and vulnerabilities. It provide the security solution to identify that the security weaknesses have been exploited, and providing active protection by terminating the session or issuing an alert.

