Vulnerabilities Assessment & Penetration Testing
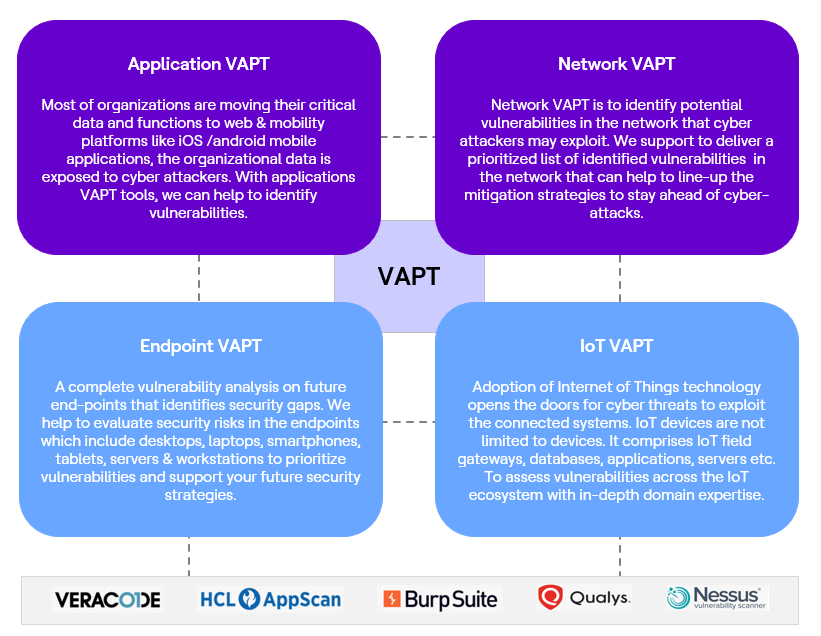
Vulnerability Assessment & Penetration Testing is also known as VAPT. It is a comprehensive security testing technique to identify security vulnerabilities in an application, network, endpoint, and cloud. By combining both vulnerability assessment and penetration testing, VAPT security audit provides an in-depth security analysis to strengthen an organization’s cyber security. Vulnerability Assessment is done by automated tools and scans the application/IT assets and notifies organizations about pre-existing security flaws. Penetration test exploits the vulnerabilities in the system & determines the security gaps.
Vulnerability assessment tools (Veracode, AppScan, BurpSuite, Qualys) find the existing vulnerabilities in the system, but do not differentiate between flaws that can be exploited to cause damage. Vulnerability scanners alert the organizations to the pre-existing security flaws in their code and network. Penetration testing attempt to exploit those vulnerabilities in a system to determine whether unauthorized access or other malicious attacks is possible and identify which flaws pose a threat to the application. Penetration tests discover exploitable flaws and measure the severity of each components. A penetration test is meant to show how damaging a flaw could be in a real attack rather than find every flaw in a system. Both together, vulnerability assessment & penetration testing tools provide a detailed analysis of the flaws that exist in an application and the risks associated with those flaws.
What is a Vulnerability Assessment?
The process of discovering and measuring known security vulnerabilities in a system is known as vulnerability assessment. It is used to evaluate of information security posture at high-level that finds flaws and suggests mitigation solutions to either eliminate or reduce those flaws to an acceptable risk level. Vulnerability Assessment follow the stages as outlined below:
- Inventory the IT assets and system resources
- Assign the monetary and contextual value to the resources
- Determine security flaws or potential risks associated to each resource
- Reduce or remove the most serious threats or attacks to critical resources
Root Cause of Vulnerabilities
Misconfiguration and bad programming methods are the main reasons for any vulnerabilities in the system. Some of the following reasons for vulnerability as below:
- Defects in software design and open-source dependencies
- Inadequately configured system which is linked to an unsecured network
- Password combinations that are ineffective or weak combination
- Infrastructure and architecture is complex
What is Penetration Testing?
Penetration Testing is a type of technique in Security Testing that uncovers vulnerabilities, threats, risks in a software application, network or web & mobile application that an attacker could exploit. The purpose of PenTest is to find all the security vulnerabilities that are present in the system being tested. It is also called Pen testing or PenTest.
Vulnerability is the risk that an attacker can disrupt or gain authorized access to the system or any data contained within it. Vulnerabilities are usually introduced by accident during software development and implementation phase. Common vulnerabilities include design errors, configuration errors, software bugs etc. Penetration Analysis depends upon two mechanisms namely Vulnerability Assessment and Penetration Testing (VAPT).
Why Penetration Testing?
Penetration is essential in an enterprise because –
- Financial sectors like Banks, Investment Banking, Stock Trading Exchanges want their data to be secured, and penetration testing is essential to ensure security
- In case if the software system is already hacked and the organization wants to determine whether any threats are still present in the system to avoid future hacks.
- Proactive Penetration Testing is the best safeguard against hackers
Types of Penetration Testing:
The type of penetration test selected usually depends on the scope and whether the organization wants to simulate an attack by an employee, Network Admin (Internal Sources) or by External Sources. There are three types of Penetration testing and they are
- Black Box Testing
- White Box Penetration testing
- Grey Box Penetration Testing
In black-box penetration testing, a tester has no knowledge about the systems to be tested. He is responsible to collect information about the target network or system.
In a white-box penetration testing, the tester is usually provided with complete information about the network or systems to be tested including the IP address schema, source code, OS details, etc. This can be considered as a simulation of an attack by any Internal sources (Employees of an Organization).
In a grey box penetration testing, a tester is provided with partial knowledge of the system. It can be considered as an attack by an external hacker who had gained illegitimate access to an organization’s network infrastructure documents.
Application Penetration Testing Methodologies
There are various methodologies or approaches which we can make use of as a reference for performing an attack.
One can take into an account the following standards while developing an attack model.
Among the following list, OWASP is the most active and there are a number of contributors. We widely focus on OWASP techniques which each development team takes into consideration before designing a web or mobile application.
- PTES − Penetration Testing Execution Standard
- OSSTMM − Open Source Security Testing Methodology Manual
- OWASP Testing Techniques − Open Web Application Security Protocol

